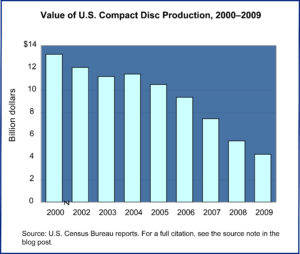
Year: 2019 and 2027
Market size: $2.75 billion and $23.98 billion, respectively
Today’s market size shows total global revenues for unified endpoint management (UEM) in 2019 and projected for 2027. UEM consists of software tools that provide a single management interface for a variety of devices (endpoints) such as desktop computers, tablets, smartphones, printers, Internet of Things devices, and wearables. UEM tools allow IT departments to configure, control, and manage devices on multiple platforms: Windows 10, macOS, Android, iOS, Chrome OS, Linux, among others. These tools also allow for simplified migration from legacy platforms to newer ones.
In 2019 there were 1,506 data breaches in the United States alone, exposing more than 164 million records. In 2018, more than 471 million records were compromised. With more people working from home, especially during the pandemic, the need for organizations to remotely manage and secure a variety of devices on third-party networks in addition to their own networks is critical. More and more employees are accessing corporate networks and data from their personal devices; the devices themselves, and the software on them, aren’t sanctioned by the companies’ IT departments. Also, employees may be working while using unsecured home or public Wi-Fi hotspots. In the past most security breaches happened within a corporate network, now breaches are increasingly coming from unsecured endpoints. Some UEM tools use zero-trust security that blocks users whenever they try to access a different part of an organization’s network. Users are not automatically granted access because they have previously been granted access. Therefore, if a breach takes place, only part of the network is compromised.
UEM evolved from mobile device management and enterprise mobility management. Mobile device management allowed IT departments to manage mobile devices remotely, but these devices were dedicated to certain limited uses. Enterprise mobility management incorporates both mobile device management as well as mobile content management — document and data security and device-specific app management. These solutions, however, take a piecemeal approach to provide security and management features for legacy, desktop, mobile, and IoT devices. UEM provides users with “a comprehensive solution that requires organization through a single pane of glass, making the management process simpler overall.”1 This unified approach also helps organizations comply with government regulations such as GDPR by allowing administrators to encrypt multiple databases and their contents while maintaining compliance regulations. UEM tools provide auditing and reporting functionality to meet these requirements.Large organizations held a 74% revenue share in 2019. This segment is expected to continue to hold the majority share through 2027. Growth is expected as more large organizations adopt a variety of endpoint solutions, complicating IT management. The increasing risk of cyber threats against large firms is also expected to spur growth. The fastest revenue growth, however, is expected to come from small and medium-sized businesses (SMEs) as they adopt more cloud-based solutions and increasingly need to secure company-owned as well as employees’ personal devices. The need to manage compliance requirements is also spurring SMEs to adopt UEM solutions.
Businesses in the telecommunications and IT sectors held the highest market share in 2019, followed by the banking, financial services, and insurance sector, and government and defense. UEM in the healthcare sector is expected to experience the highest growth as more healthcare institutions adopt mobile and other IoT devices to remotely communicate, collaborate, and share critical information. Increased adoption of blood pressure monitors, wearable devices, and other cloud-based devices will also contribute to the growing adoption of UEM solutions.
North America claimed 42% of the market in 2019 and is expected to continue to hold the largest share through 2027 as companies continue to invest in advanced technologies to simplify their business operations. The Asia Pacific region is expected to experience the fastest growth over this time period. Organizations in this region are increasingly adopting mobile devices and IoT applications as well as cloud-based solutions and “bring your own device” policies.
The market is fragmented with both large and emerging companies offering a range of UEM solutions. In some cases, UEM vendors are forming partnerships and collaborations in addition to acquiring companies to maintain their market share. Some major companies offering UEM solutions include 42Gears Mobility Systems Pvt. Ltd., BlackBerry Ltd., Citrix Systems Inc., IBM, Matrix42 AG, Microsoft, MobileIron Inc., Sophos Ltd., SOTI Inc., Zoho Corp., Ivanti, and VMWare Inc.
1 Source: Tess Hanna, “UEM or EMM: What’s Better for Endpoint Management? Mobility Management Solutions Review, October 26, 2018 available online here.Sources: “Unified Endpoint Management Market Size $23.98 Billion by 2027: Grand View Research, Inc. – Press Release – Digital Journal,” Journal of Cyber Policy, October 8, 2020 available online here; “Unified Endpoint Management Market Size $23.98 Billion by 2027: Grand View Research, Inc.,” Digital Journal Press Release available online here; “Unified Endpoint Management Market Size, Share & Trends Analysis Report by Component (Solution, Services), by Organization Size (SMEs, Large Enterprises), by Vertical, by Region, and Segment Forecasts, 2020 – 2027,” Grand View Research Report Summary, September 2020 available online here; “What is Unified Endpoint Management?” VMware Glossary available online here; Tess Hanna, “UEM or EMM: What’s Better for Endpoint Management? Mobility Management Solutions Review, October 26, 2018 available online here; J. Clement, “Cyber Crime: Number of Data Breaches and Records Exposed 2005-2020,” Statista, October 1, 2020 available online here.
Image source: Gerd Altmann, “binary-one-cyborg-cybernetics-2302728,” Pixabay, May 11, 2017 available online here.






 Globally the number of cyber security incidents increased 1,637% from 3.4 million incidents in 2009 to more than 59 million incidents in 2015. In the United States the number of data breaches alone increased from 446 in 2007 to 1,579 in 2017. According to Steve Langan, chief executive at Hiscox Insurance, cybercrime cost the global economy more than $450 billion dollars in 2016.
Globally the number of cyber security incidents increased 1,637% from 3.4 million incidents in 2009 to more than 59 million incidents in 2015. In the United States the number of data breaches alone increased from 446 in 2007 to 1,579 in 2017. According to Steve Langan, chief executive at Hiscox Insurance, cybercrime cost the global economy more than $450 billion dollars in 2016.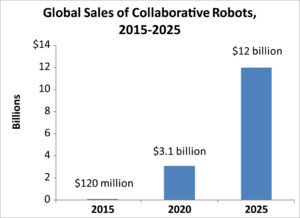 Collaborative robots, or co-bots, are robots that work alongside human workers. Many workers are wary of the increased use of robots in general, fearing the loss of their jobs. M.I.T. and Boston University estimated that up to six people lose their jobs for each robot per 1,000 workers a company adds. Employers, however, cite increased productivity, cost savings, and healthier work environments when robots are used in the workplace. Robots can work in hazardous jobs or do repetitive tasks thereby reducing worker injuries.
Collaborative robots, or co-bots, are robots that work alongside human workers. Many workers are wary of the increased use of robots in general, fearing the loss of their jobs. M.I.T. and Boston University estimated that up to six people lose their jobs for each robot per 1,000 workers a company adds. Employers, however, cite increased productivity, cost savings, and healthier work environments when robots are used in the workplace. Robots can work in hazardous jobs or do repetitive tasks thereby reducing worker injuries.